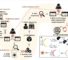
We started by mapping the entire network, comparing our results to what the hospital’s IT staff knows (think they know) – since we discovered a mess, we started a Sisyphean process of pinging, querying walking around the hospital searching for devices, and creating an updated network architecture map. The stuff we discovered was scary, funny and shocking. At the second stage, we conducted a penetration test on each medical device, software and system we could find – that includes Imaging systems of all kinds and sizes, Cardiac pacemakers, Electromechanical technology, Hospital hardware, Laboratory equipment, Gas and drug delivery systems, Surgical instruments, Medical monitoring devices, doctor’s applications, internal portals and databases, rogue WIFI access points, physical security vulnerabilities and more, this time our findings were terrifying, hilarious, and outrages!
![]() Подписывайтесь на канал “Engine.MD” в Telegram, чтобы первыми узнавать о новостях и эксклюзивных материалах.
Подписывайтесь на канал “Engine.MD” в Telegram, чтобы первыми узнавать о новостях и эксклюзивных материалах.